AzureAD - Client Credentials
Setup AzureAD
Add New App Registration
Go to App registrations > New registration.
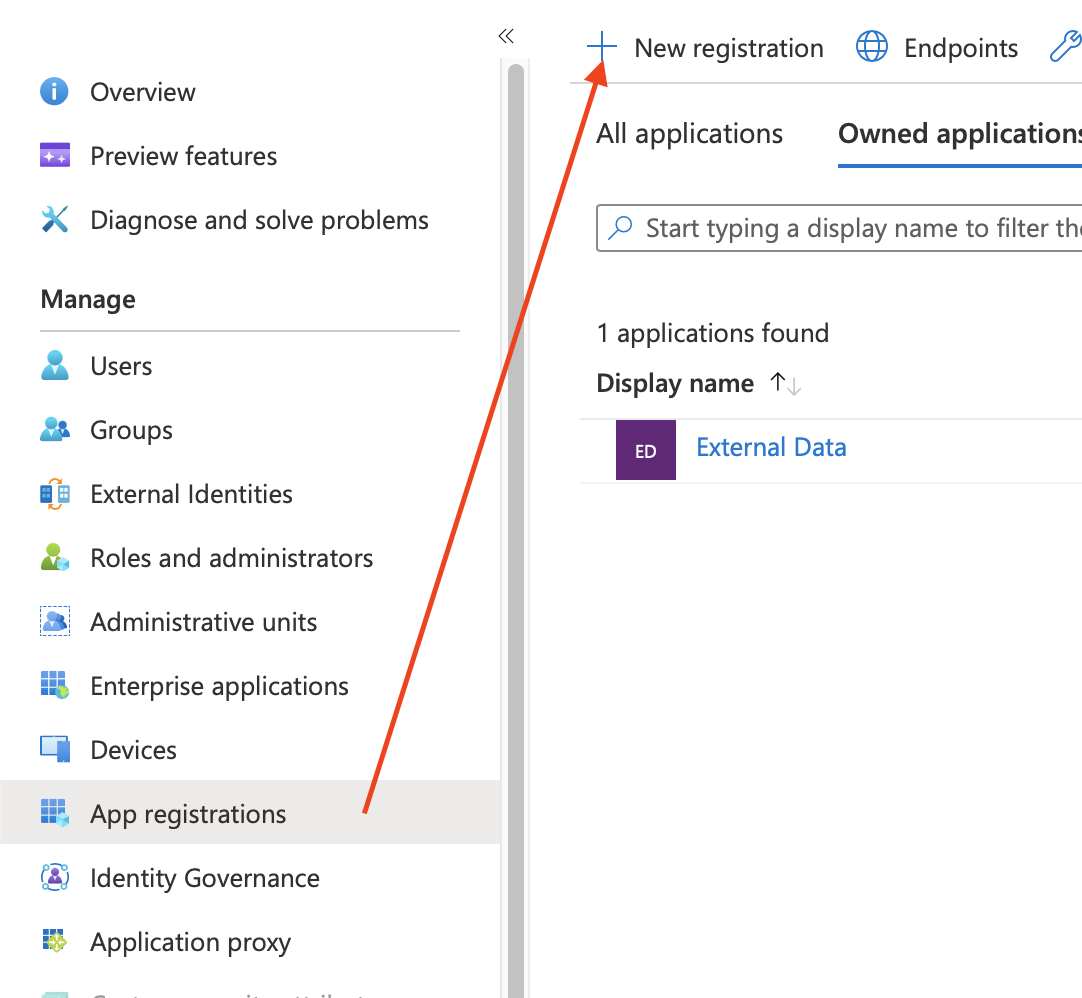
Add a new registration.
Tipp: When naming the new app, choosing a recognisable name like External Data for Jira Fields can help you to properly identify the application later.
Certificates & Secret
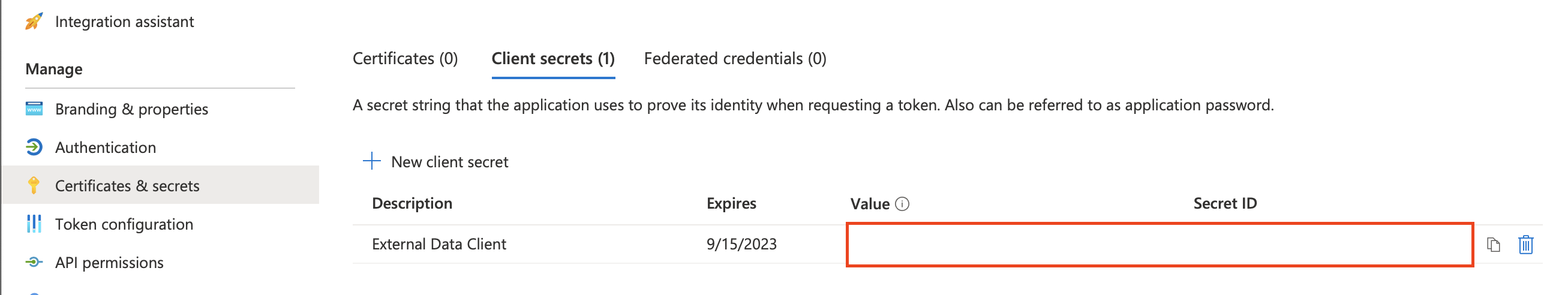
Go to Certificates & secrets > Client secrets > New client secret
Add a meaningful description and set an expiration date. Keep in mind that you’ll have to update the data source once the secret expires.
Important: Please be sure to note the Secret Value, which will only be visible immediately after creation. You will need this value later when setting up the data source.
API Permissions
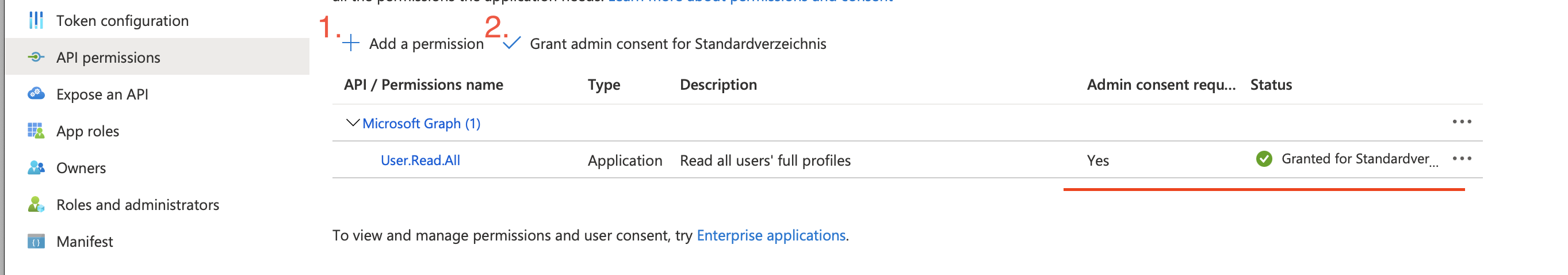
Go to API permissions > Add a permission
Select Microsoft Graph (or another service you want to access) > Application permissions
Now select the API / Permission name you want to add. In our example we use the User.Read.All permission.
This permission needs Admin consent so we allow Grant admin consent for ...
Collect Endpoint & Client ID
Since you will need the endpoint and client ID later on, we recommend to note them down.
Go to Overview > Endpoints and copy the following endpoint:
OAuth 2.0 token endpoint (v2)Go to Overview > Application (client) ID and note the Client ID value.
Setup External Data
Create New Data Source
Go to External Data for Jira Fields > Data Sources > Add Data Source
URL
You can find a complete list of available Azure API endpoints here.
In this example we use the following endpoint to access the profiles of the users:
https://graph.microsoft.com/v1.0/usersAuthentication:
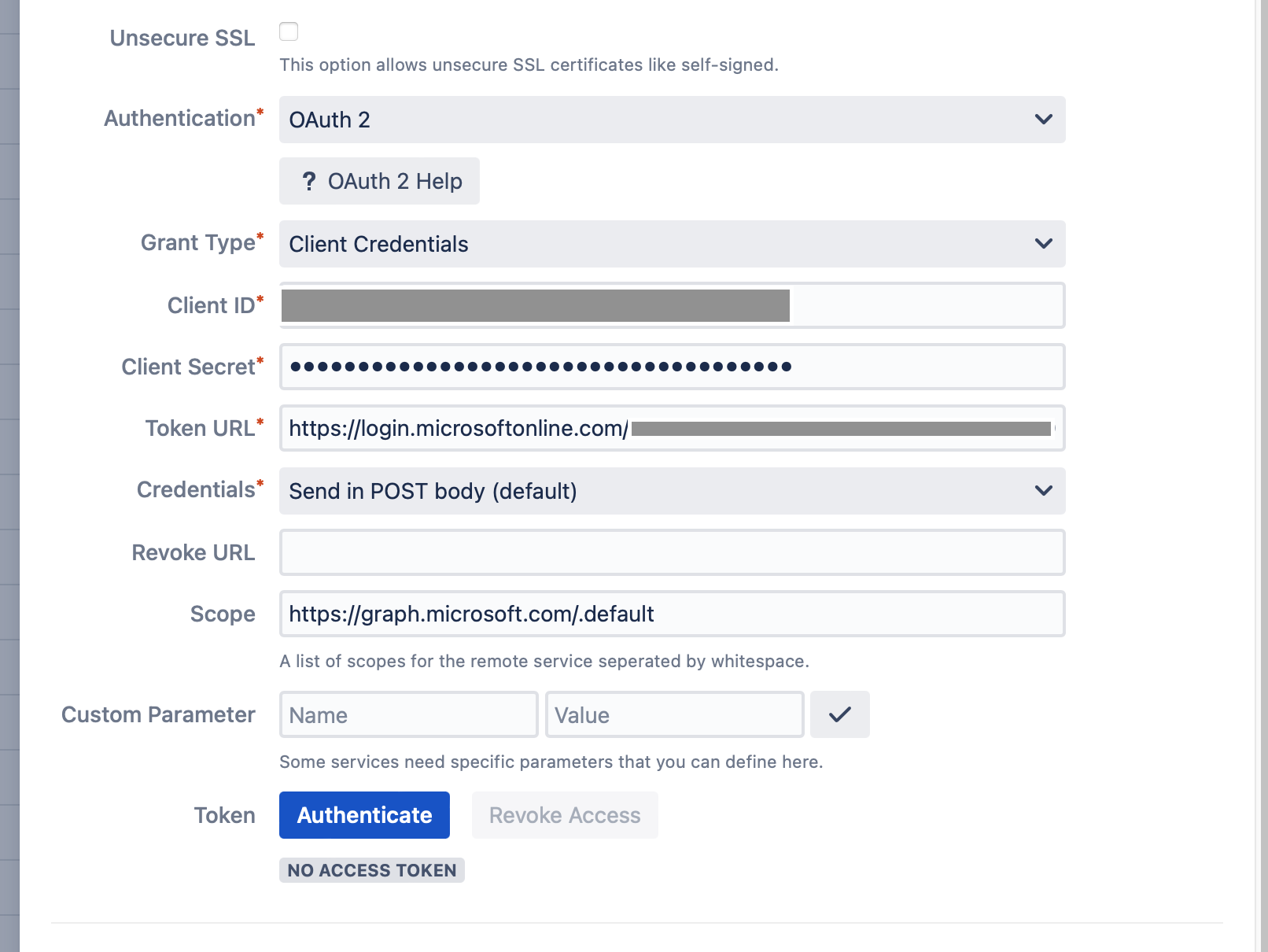
Select Authentication OAuth2 > Grant Type > Client Credentials
Client ID & Client Secret
Enter the Client ID, which you can find here: Overview > Application (client) ID
Client Secret is the secret value created in the Certificates & secrets section. Please insert the noted value here.
Endpoints
Endpoints are service specific URLs for receiving an access token. Since we are using the client credentials flow, we only need the token endpoint.
Token Endpoints:
Token Url: https://login.microsoftonline.com/{tenant}/oauth2/v2.0/tokenScopes
Scopes define the permission to specific parts of the data. Since we are using the Client Credentials Flow, we simply set the scope to::
https://graph.microsoft.com/.defaultMake sure that an administrator grants you the required permissions that you need for the settings in the Azure backend.
Authenticate
Click Authenticate to retrieve your access token.
Save and test the data source to ensure that everything works as intended.
