Restrict Access to Cloning
Deep Clone for Jira supports restricting access without changing Jira user groups. Restrict access can limit the spaces (projects) work items can be cloned into by different users for Single Clone, Epic/Tree Clone, or Bulk Clone.
Read more about giving or removing access for users or user groups under User Permissions.
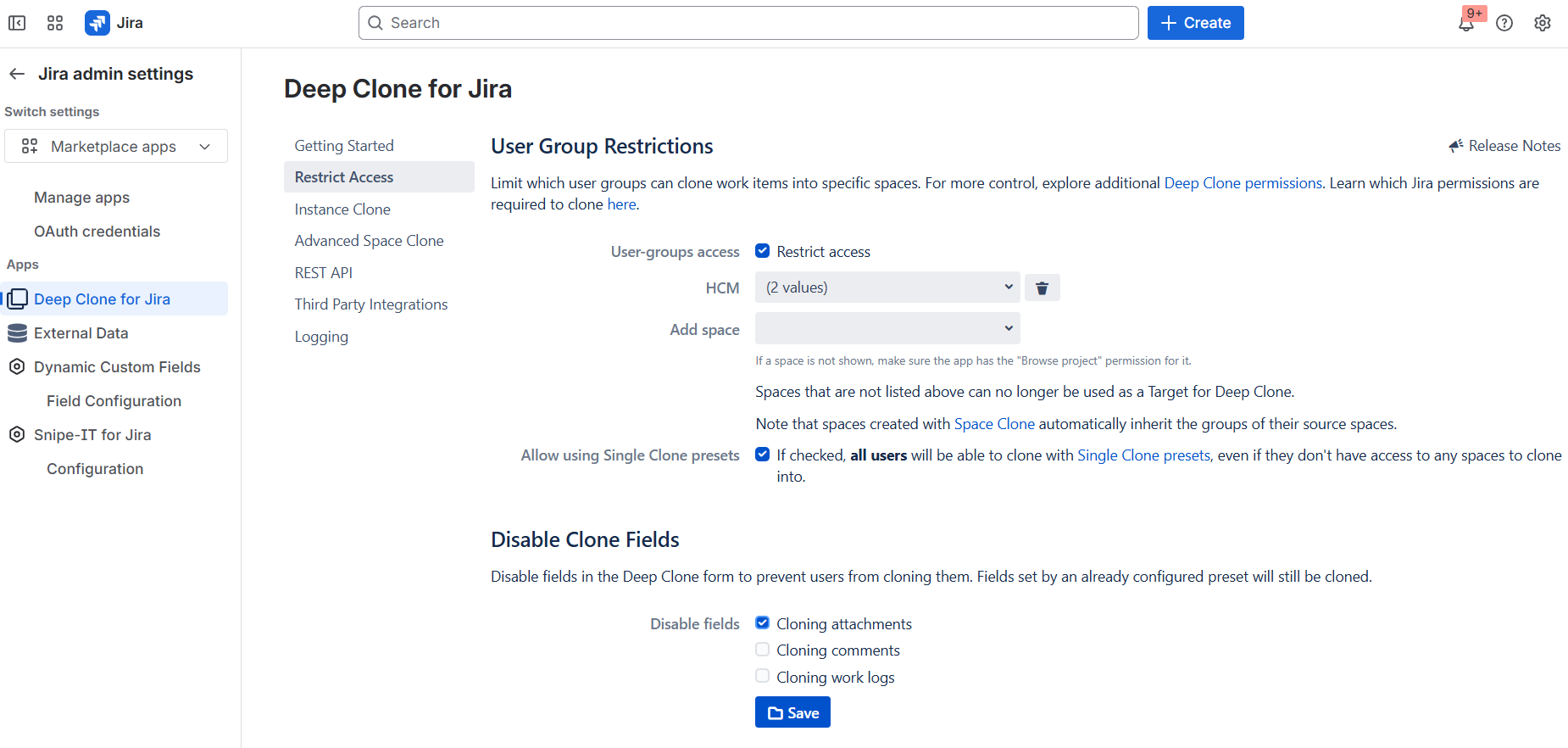
You can configure Deep Clone for Jira specific restriction under ⚙️ Settings > Marketplace apps > Deep Clone for Jira > Restrict access
If Restrict access is enabled, but no spaces are configured, no user will be able to select a Target space in Single Clone, Epic/Tree Clone, or Bulk Clone.
Check Restrict access to user-groups
Select the space (project) in the drop-down you want to restrict cloning into
Select group(s) that should still be allowed to clone into this space
Save
Users need to have the “Create Issue” permission for this space in order to be able to Deep Clone into it, regardless of the “Restrict access” settings below.
Restrict access also allows restricting the following Deep Clone features:
Disable cloning attachments
Disable cloning comments
Disable cloning work logs
Data Security Policies | App Access Rules
A Jira Organization Administrator can also restrict access for Deep Clone for Jira with data security policy on https://admin.atlassian.com/ under Security > Data security policies. There, it’s possible to create an app access rule to limit access for Deep Clone (or other apps) to specific spaces.
What will my users experience?
When the Block app access option is selected, users will no longer see apps in Confluence spaces or Jira spaces in which they are blocked, and the apps will behave as though they have been uninstalled. Links to apps will no longer be accessible, and supporting app functions such as inline dialogues will no longer appear. When Allow app access is selected, apps will appear as normal and all app functions will be available.

